Lab Deployment
Lab Overview
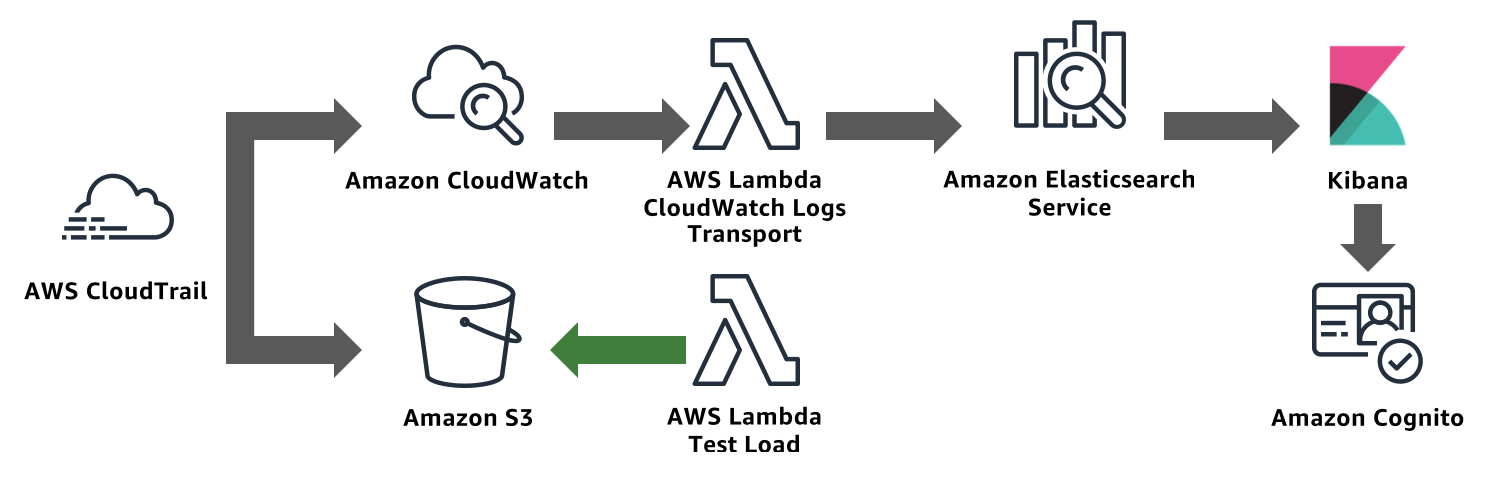
In this lab, you will use CloudFormation to deploy
An AWS CloudTrail Trail. CloudTrail collects logs from AWS services when you make calls to their APIs
An Amazon S3 bucket to serve as the destination for CloudTrail logs
An Amazon CloudWatch Logs log group for CloudTrail to deliver logs
An Amazon Elasticsearch Service domain. CloudWatch Logs (via Lambda) sends CloudTrail’s log lines to this Amazon Elasticsearch Service domain
An Amazon Cognito User Pool and Identity Pool. Amazon Elasticsearch Service’s Kibana integrates with Cognito to provide a login experience for Kibana. The template also includes a custom Lambda function that creates a Cognito user and Cognito domain for serving login requests
[OPTIONAL] A second CloudFormation template provides a second S3 bucket and a Lambda function to write objects to that bucket. You can use this Lambda to generate S3 API calls and enable logging of those calls to generate traffic for your domain
Send CloudTrail logs to Amazon Elasticsearch Service
Deploy the first CloudFormation Stack
Sign in to the AWS Management Console
Select US East (N. Virginia) in the region selector
In the search box, type CloudFormation and click CloudFormation.
Click Create Stack (If you don’t have any stacks, click the Create New Stack).
Click Specify an Amazon S3 template URL radio button and paste the following URL in the text box.
https://s3.us-east-2.amazonaws.com/search-sa-log-solutions/cloudtrail/CT-CWL-AES.json
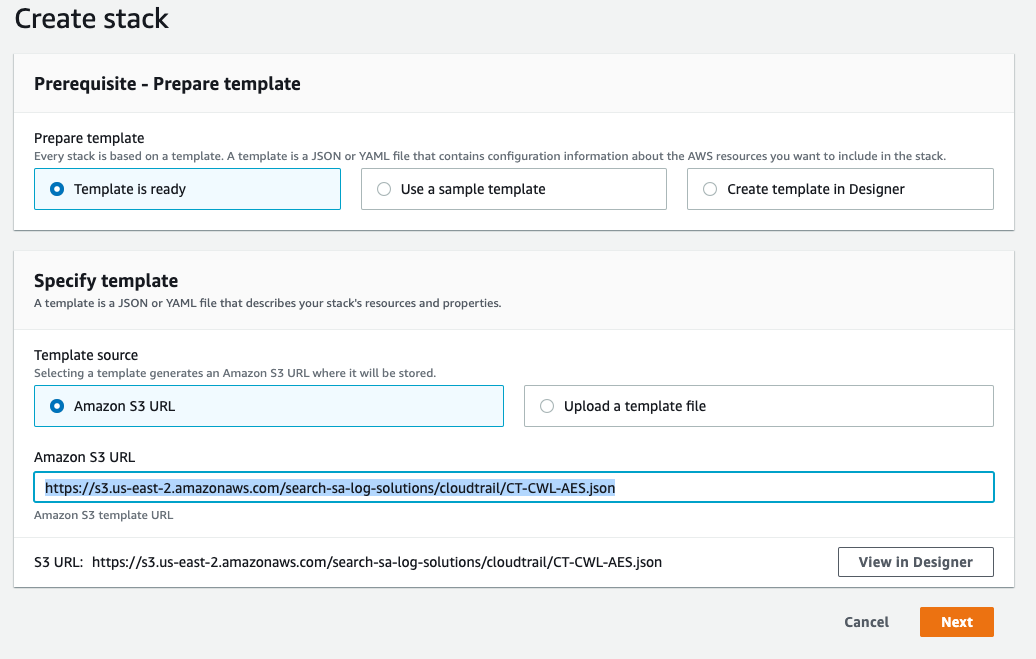
Click Next.
Give your stack a Stack name. Leave the ES Version as 6.3, and set a Stack Prefix. The stack prefix can be any short string and will be used as a prefix for all of the resource names in the stack.
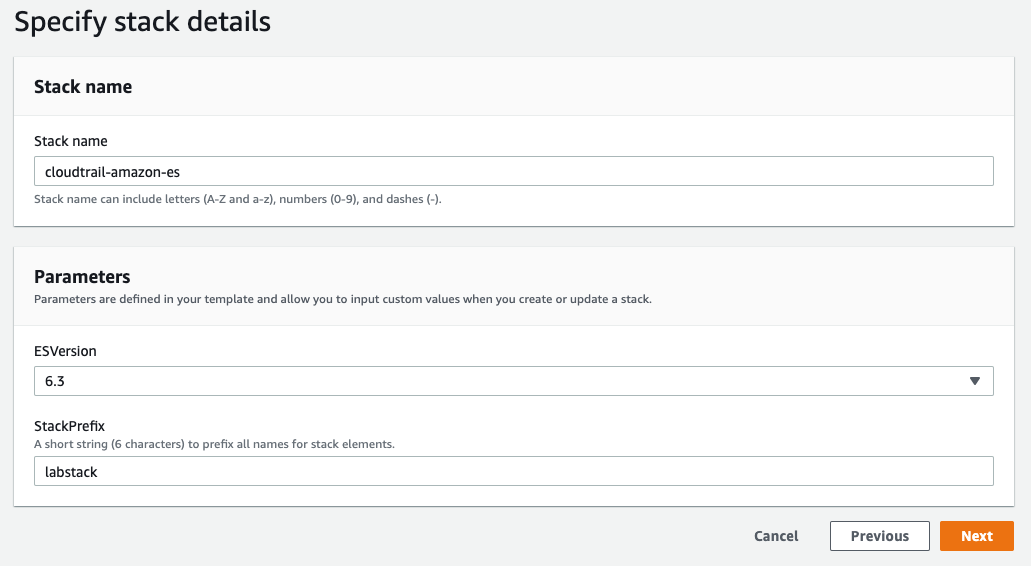
Click Next.
Leave the Options and Advanced Options at their defaults, scroll down and click Next.
On the Review page, scroll down and check the box next to I acknowledge that AWS CloudFormation might create IAM resources with custom names.
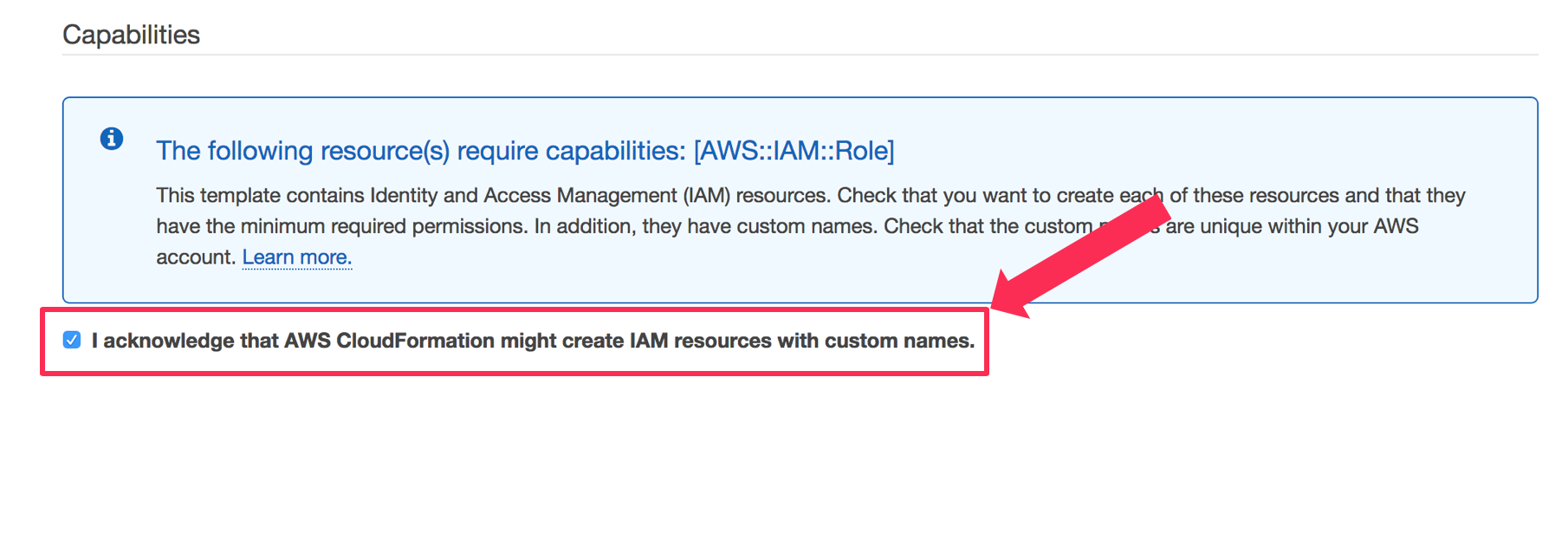
Click Create Stack.
The stack will take about 15 minutes to deploy. Wait until CloudFormation shows the stack Status as CREATE_COMPLETE (You will need to click the refresh button on the right-hand corner to see if the status has changed)

Enable Cognito sign on for Amazon Elasticsearch Service
 Click Services and type Elasticsearch. Click Elasticsearch Service.
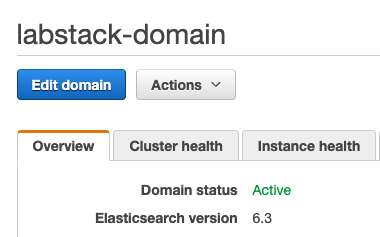
Click Services and type Elasticsearch. Click Elasticsearch Service.Looking at the Dashboard find and click on the domain you just created, named <stack prefix>-domain to view the domain’s dashboard.
Click Edit Domain.
Scroll down to the Amazon Cognito authentication section, and click Enable Amazon Cognito for authentication.
Leave the Region as US East (N. Virginia)
In the Cognito User Pool drop down, select the user pool named <stack prefix>UserPool.
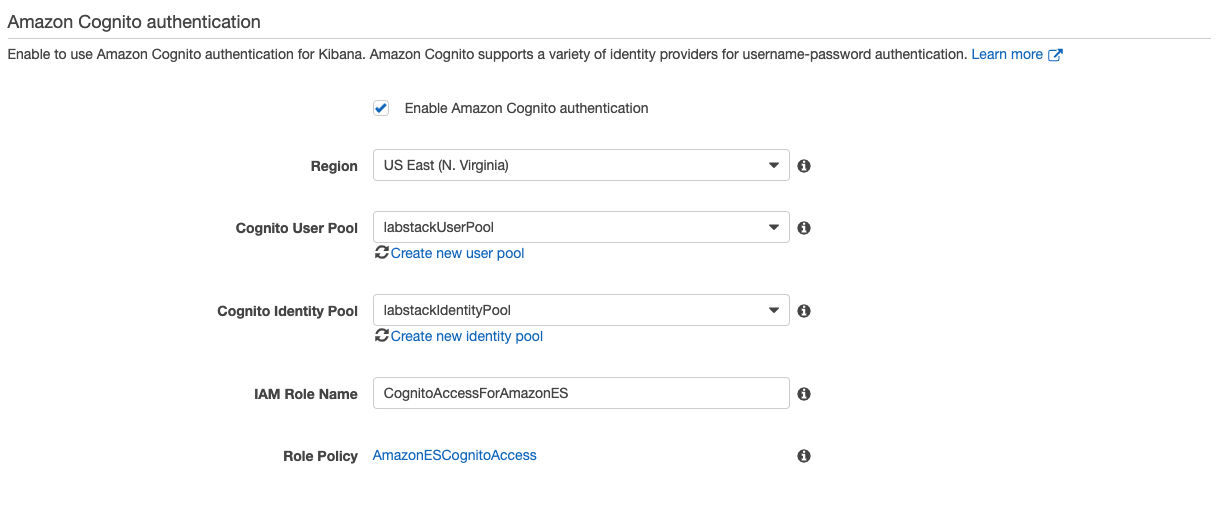 In the Cognito Identity Pool drop down, select the identity pool named <stack prefix>IdentityPool.
In the Cognito Identity Pool drop down, select the identity pool named <stack prefix>IdentityPool.Click Submit.
Your domain will enter the Processing state. This will take approximately 10 minutes to complete. Wait until the domain changes to the Active state before going on to the next section.
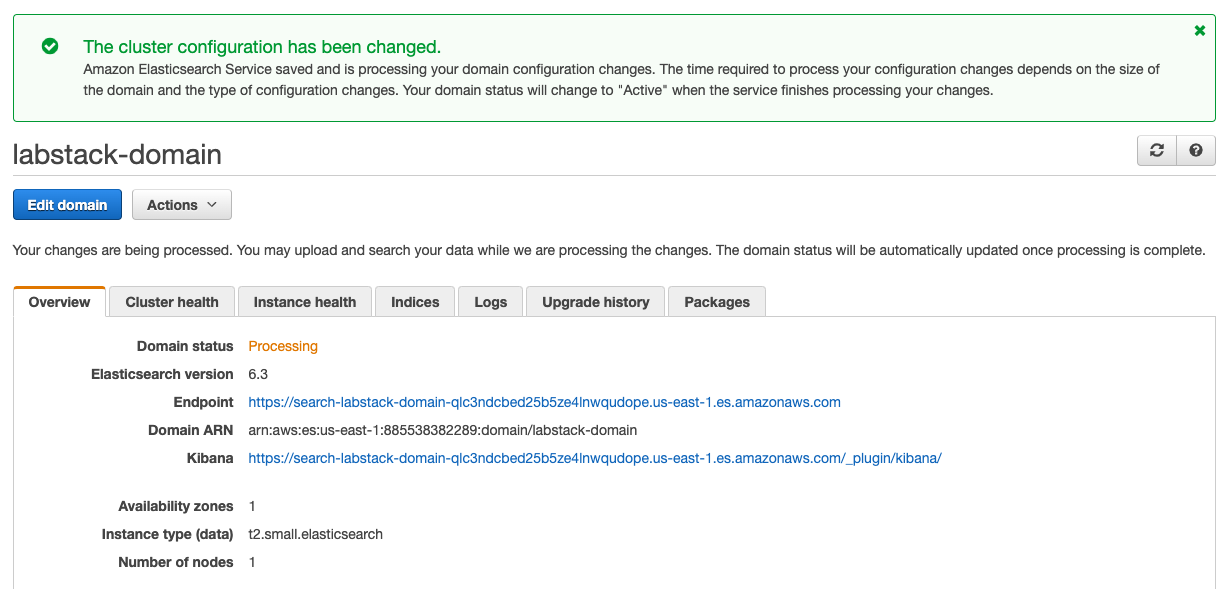
Start streaming logs from CloudWatch Logs to Amazon ES
From the Services Dropdown, select the Cloudwatch Service.
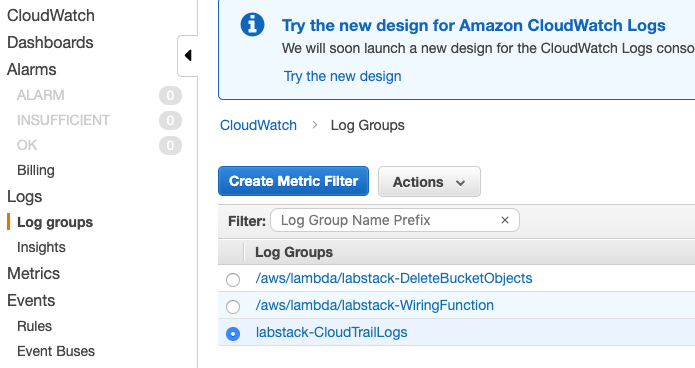
From the CloudWatch console select Logs Groups in the left-hand navigation.
Locate the log group associated with the lab <stack prefix>-CloudTrailLogs.
Click the radio button next to your log group (don’t click the name of the group itself).
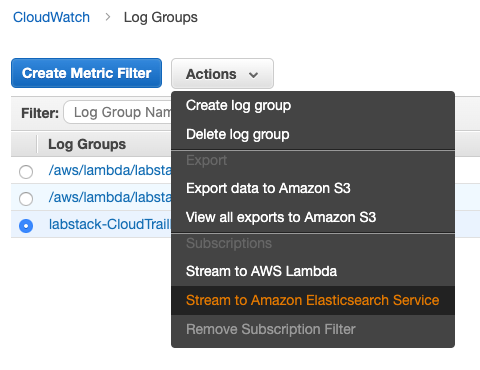
From the Actions menu, select Stream to Amazon Elasticsearch Service.
Select your domain from the Amazon ES cluster menu.
From the Lambda IAM Execution Role menu, select <stack prefix>-CWLRoleForStreaming.
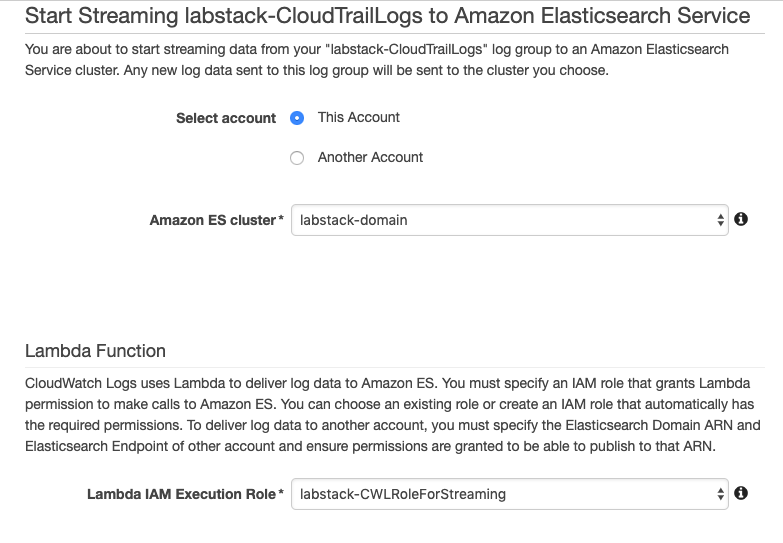
Click Next.
For Log Format, select AWS CloudTrail.
Leave the other fields at their defaults and click Next.
On the Review page, click Next.
Click Start Streaming.